Whether all of your data is stored in a traditional on-site data center or in a cloud environment, protecting that sensitive data is of upmost importance. However, the way one approaches on-site data storage security and cloud computing IT Security is different. Having your data in the cloud introduces areas of vulnerability, threats, and challenges and needs to be approached with that in mind.
Organizations typically have a mix of traditional IT and cloud services, so your security solutions need to protect both. The security controls in place for your on-site data may not cut the mustard when it comes to protecting your sensitive client information in the cloud.
The good news is that there ARE IT Security solutions that are more than capable to address the challenges that arise from Cloud Computing. And in truth, information stored on the cloud is likely to be more secure than files, images, videos, and data stored on your own devices? Cloud companies rely on strong cybersecurity measures to protect sensitive data.
Cloud Security Threats
Data Breaches
With the rise of ransomware and phishing scams, it is no secret that data breaches are consistently amongst the top threats listed when IT Professionals are queried. Data breaches not only damage business reputations but also pose significant legal liabilities and the potential for loss of intellectual property. Businesses need to define the value of its data and the impact of its loss in comprehensive business continuity plans. They need to identify who has access to their data and determine how to limit access and train stakeholders to keep their access points private and secure. Businesses need strong, reliable, and tested incident response plans in place with their cloud service providers.
Lack of Cloud Security Architecture and Strategy
This is a fancy way of saying that when it comes to migrating data to the cloud, taking short cuts causes harm. Too many times speed takes precedence over security. Your security architecture needs to align with your business goals and objectives. Your security architecture framework needs to be well developed and implemented as well as continuously monitored and threat models kept up to date.
 Lackluster Access Management
Lackluster Access Management
Another threat to cloud computing security is poor management and training of just who has access to your data. Are your employees well trained in protecting their credentials? Do you use multi-factor authentication? How strong are your passwords and how often are you requiring your employees to change them? Are former employees’ credentials promptly revoked?
Yes, yes. We know this is a hassle. But when it comes to protecting your data, your employees are not just your weakest link in the IT Security chain, but also your greatest asset.
Account Hijacking
As phishing scams become more prevalent, more and more bad actors are allowed access to private accounts. Once a hacker has access to a system using a legitimate account, they can wreak havoc including such things as data loss, theft, financial fraud or stopping service. Once again, training your employees to recognize phishing scams is your best defense.
So How is Cloud Security Different?
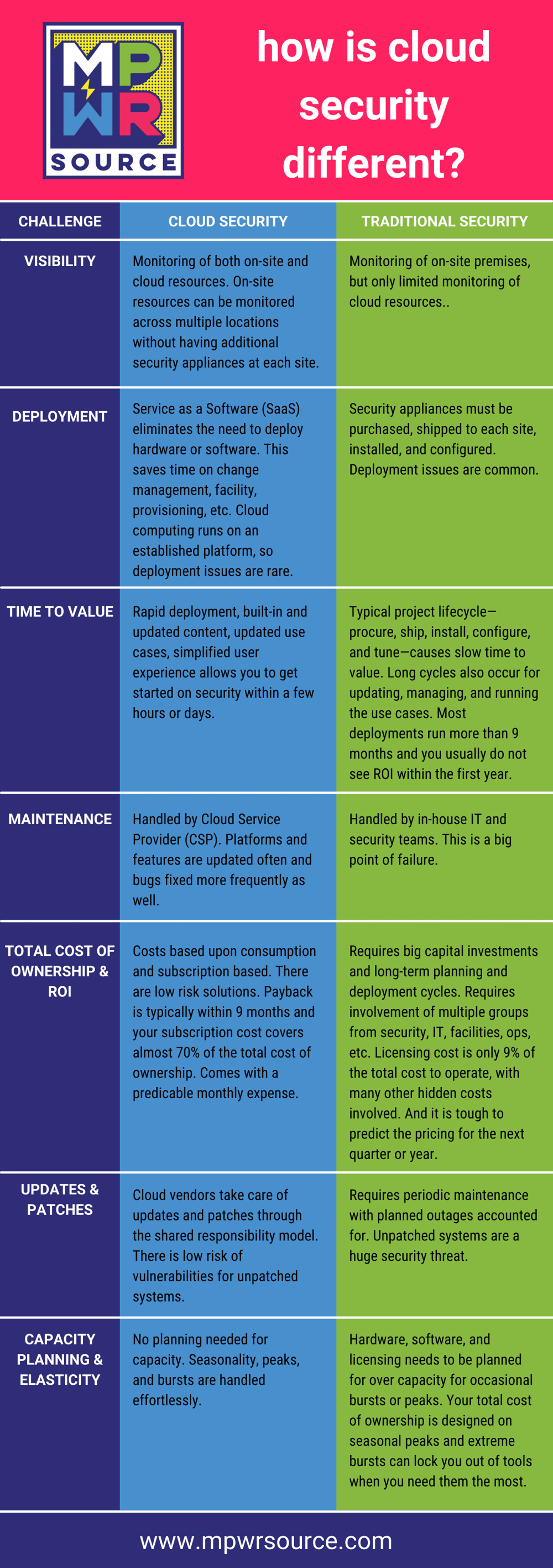
Cloud security is different for a reason. The rapid changes of the needs of business owners necessitate a security system that is adaptable. One that is dynamic and fluid and that can adapt with its owner’s needs. Cloud specific security is the only way to effective secure resources held within cloud computing environments.
Tips for Mitigating Cloud Computing Security Risks:
- Regular Backups
- Multi-Factor Authentication
- Limit User-Level Access
- Data Encryptions
- Choose your Cloud Provider Wisely. Know where they are storing your data, be it here in the United States or abroad. Choose a cloud service provider that can take into account the regulatory and compliance needs of your industry.
- Reset Your Passwords Regularly.